Man in the Middle Attacks Can Be Prevented by Using __________.
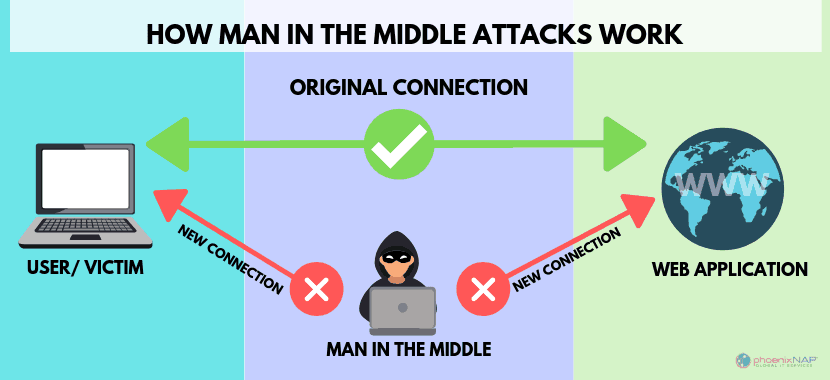
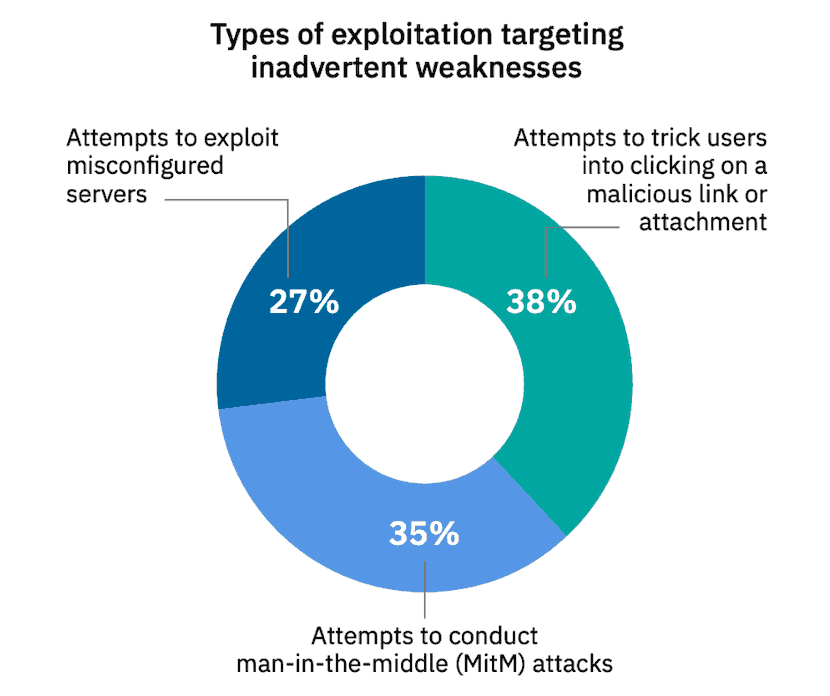
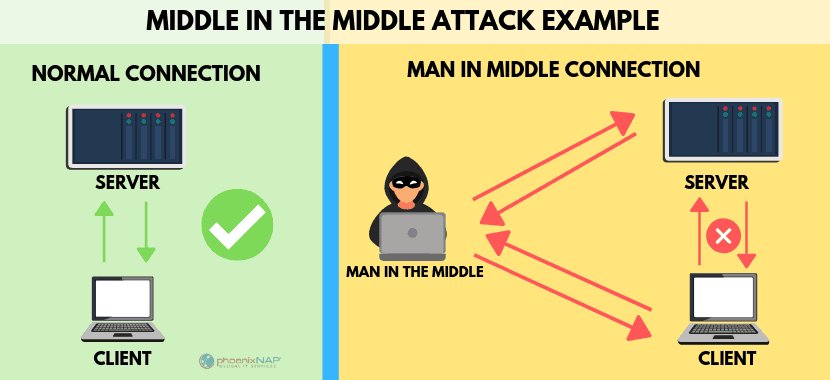
In this article y'all will acquire: A Human-in-the-Centre (MITM) attack happens when a hacker inserts themselves between a user and a website. This kind of assault comes in several forms. For example, a imitation banking website may be used to capture financial login information. The fake site is "in the middle" betwixt the user and the bodily bank website. Attackers have many dissimilar reasons and methods for using a MITM attack. Typically, they're trying to steal something, similar credit bill of fare numbers or user login credentials. Sometimes they're snooping on private conversations, which might include trade secrets or other valuable information. One thing that almost all attacks have in common is the bad guy is pretending to be someone (or a website) you trust. If you lot've ever used a laptop in a coffee shop, yous may take noticed a pop-up that says "This network is non secure." Public wi-fi is usually provided "as-is," with no guarantees over the quality of service. All the same, unencrypted wi-fi connections are easy to eavesdrop. It's much like having a conversation in a public eating house – anyone can heed in. You can limit your exposure by setting your network to "public," which disables Network Discovery. This prevents other users on the network from accessing your organisation. Another Wi-Fi Eavesdropping set on happens when a hacker creates its own wi-fi hotspot, called an "Evil Twin." They make the connection look just like the accurate one, down to the network ID and passwords. Users may accidentally (or automatically) connect to the "evil twin," allowing the hacker to snoop on their activity. In this blazon of cyber security attack, a hacker compromises a user'due south e-mail account. Ofttimes, the hacker silently waits, gathering information and eavesdropping on the e-mail conversations. Hackers may accept a search script that looks for specific keywords, similar "depository financial institution" or "surreptitious Democrat strategies." Email hijacking works well with social engineering science. Hackers might use information from a hacked email account to impersonate an online friend. They may utilize as well use spear-phishing to manipulate a user to install malicious software. As mentioned before, all systems connected to a network have an IP address. Many corporate intranet networks give each organisation its ain IP address. In IP spoofing, hackers mimic the IP address of an authorized device. To the network, the device looks similar it's approved. This can permit an unauthorized user to infiltrate a network. They may stay silent, and record activity or they may launch a Denial of Service (DoS) attack. IP spoofing can as well be used in a MITM attack by standing between 2 systems: Organisation A ====== Hacker ====== System B System A and Arrangement B think they're talking to each other, merely the hacker is intercepting and talking to both. According to IBM X-Forcefulness's Threat Intelligence 2022 Index, 35% of exploitation activity involved attackers attempting MITM attacks. Image source: IBM Threat Index The internet works by numeric IP addresses. For example, i of Google'south addresses is 172.217.fourteen.228. Most websites use a server to translate that address to a catchy name: google.com, for instance. The server that translates 127.217.14.228 into "google.com" is called a Domain Proper name Server, or DNS. A hacker can create a simulated DNS server. his is called "spoofing." The fake server routes a real website name to a unlike IP address. The hacker can create a phony website at the new IP accost that looks just like a 18-carat website. Once you visit the fake site, an attacker can gain admission to your sensitive information and personal data. It's not currently possible to duplicate an HTTPS website. However, security researchers have demonstrated a theoretical method for bypassing HTTPS. The hacker creates a web address that looks like an accurate address. Instead of regular characters, it uses letters from foreign alphabets. This appears as spam emails you may accept seen with strange characters. For example, Rolex might be spelled Rólex. SSL stands for Secure Socket Layer. SSL is the encryption protocol used when you lot encounterhttps:// in front end of a web address, not http://. With SSL Stripping the hacker intercepts and forwards traffic from a user: User ====== Hacker ====== Encrypted website The user tries to connect to the encrypted website. The hacker intercepts and connects to the encrypted site on behalf of the user. Often, the hacker creates a duplicate website to display to the user. The user thinks they are logged in to the regular website, but it'south actually what the hacker wants them to see. The hacker has "stripped" the SSL protocol out of the user'south network connectedness. This type of Human being-in-the attack is typically used to compromise social media accounts. With nearly social media sites, the website stores a "session browser cookie" on the user's machine. This cookie is invalidated when the user logs off. But while the session is active, the cookie provides identity, access, and tracking information. A Session Hijack occurs when an attacker steals a session cookie. This can happen if the user'southward motorcar is infected with malware or browser hijackers. It can besides happen when an attacker uses a cantankerous-scripting XSS assault – where the assailant injects malicious lawmaking into a oftentimes-used website. ARP stands for Address Resolution Protocol. A user sends out an ARP asking, and a hacker sends a faux reply. In this example, the hacker is pretending to be a device like a router, which allows them to intercept traffic. This is typically express to local area networks (LAN) which use the ARP protocol. This is a type of assail that exploits vulnerabilities in web browsers. Trojan horses, reckoner worms, Java exploits, SQL injection attacks, and browser add-ons can all be attack vectors. These are often used to capture fiscal information. When the user logs in to their bank account, malware captures their credentials. In some cases, malware scripts can transfer funds, then change the transaction receipt to hide the transaction. In the graphic below, an assaulter (MITM) inserted themselves in-betwixt betwixt the client and a server. As the hacker now controls communication, they can intercept information that is transferred, or interject other data, files, or data. Use a Virtual Private Network (VPN) to encrypt your web traffic. An encrypted VPN severely limits a hacker's ability to read or modify web traffic. Exist prepared to preclude data loss; accept a cyber security incident response plan. Secure your network with an intrusion detection system.Network administrators should be using adept network hygiene to mitigate a human-in-the-center attack. Clarify traffic patterns to identify unusual behavior. Your network should have strong firewalls and protocols to foreclose unauthorized access. Use third-party penetration testing tools, software, and HTTPS encryption to assist detect and block spoofing attempts. Install active virus and malware protection that includes a scanner that runs on your arrangement at boot. MITM attacks often rely on malware. Running updated anti-virus software is imperative. Encryption is the all-time defense to protect confronting intercepted communication. The well-nigh effective method to finish email hijacking is to enable two-factor authentication. That means that, in add-on to your countersign, yous have to provide another vector of authentication. One example is Gmail's combination of a password and a text to your smartphone. Sentinel out for phishing emails every bit they are the most mutual set on vector. Advisedly examine links before clicking. Just install browser plug-ins from reputable sources. Minimize the potential of attacks past signing out unused accounts to invalidate session cookies. Forcefulness encryption by typinghttps at the beginning:https://www.website.com If you expect an encrypted connection only don't have one, stop what yous're doing and run a security scan. If you apply Google Chrome, install a chrome security extension, like HTTPS Everywhere, which forces an SSL connexion whenever possible. You lot should come across a green or grey padlock merely to the left of the web address in your browser. If you ever meet a cherry padlock, that means there is something incorrect with the encryption — double check domain names and your browser earlier visiting an insecure site. Disable "Punycode back up" (for rendering characters from different languages) on your browser. Add an enterprise password management solution; this volition avoid motorcar-filling passwords on a nefarious site. Remember, mobile security best practices. Mobile applications are often targeted. Avoid using public wifi networks. If you must apply public wi-fi, configure your device to crave a manual connection. MITM attacks can exist hard to detect while they are occuring. The best way to stay safe is consistantly implementing all the prevention all-time practices to a higher place. Be enlightened that some attacks are a form of social engineering. If something doesn't seem right nigh a website or email, take a few minutes to dig a little deeper. Detecting an set on is difficult, but they tin can be prevented. Many Human In the Heart attacks can be prevented with good network hygiene, such as firewalls and security protocols. It is important to supplement these efforts by being mindful of your network habits. Learn how PhoenixNAP proactively manages, detects, and responds to security indicators with our Threat Management Intelligence Services.
What is a Man in the Center Attack? How Does it Work?
Types of Human-in-the Middle Attacks
Wi-Fi Eavesdropping
Email Hijacking
IP Spoofing Attacks
DNS Spoofing
HTTPS Spoofing
SSL Stripping
Session Hijacking
ARP Spoofing
Man-in-the-Browser
Real Life Human being-in-the-Eye Assault Case
Man in the Middle Assail Prevention
Network Security
Secure Your Communications
Use bones cyberspace security hygiene on all devices, including mobile applications.
Protect your arrangement from falling victim
richardsgicarearse.blogspot.com
Source: https://phoenixnap.com/blog/man-in-the-middle-attacks-prevention
0 Response to "Man in the Middle Attacks Can Be Prevented by Using __________."
Post a Comment